Azure Integration
StackGuardian offers two secure methods for connecting your Azure Service Principal, each tailored for different security and operational needs. To create a connector with StackGuardian, follow these steps:
-
Create StackGuardian App in Azure: Begin by registering your application in Microsoft Entra ID to establish its identity.
-
Create the Service Principal: After registering the app, configure the service principal using one of these methods:
- Using a Client Secret - Employs a secret key for authentication.
- Using Workload Identity - Leverages Azure’s identity federation for enhanced security.
After completing the app registration in your Microsoft Entra ID, ensure the application has read-access to your desired subscriptions and that correct credentials are provided to StackGuardian.
Create StackGuardian App in Azure
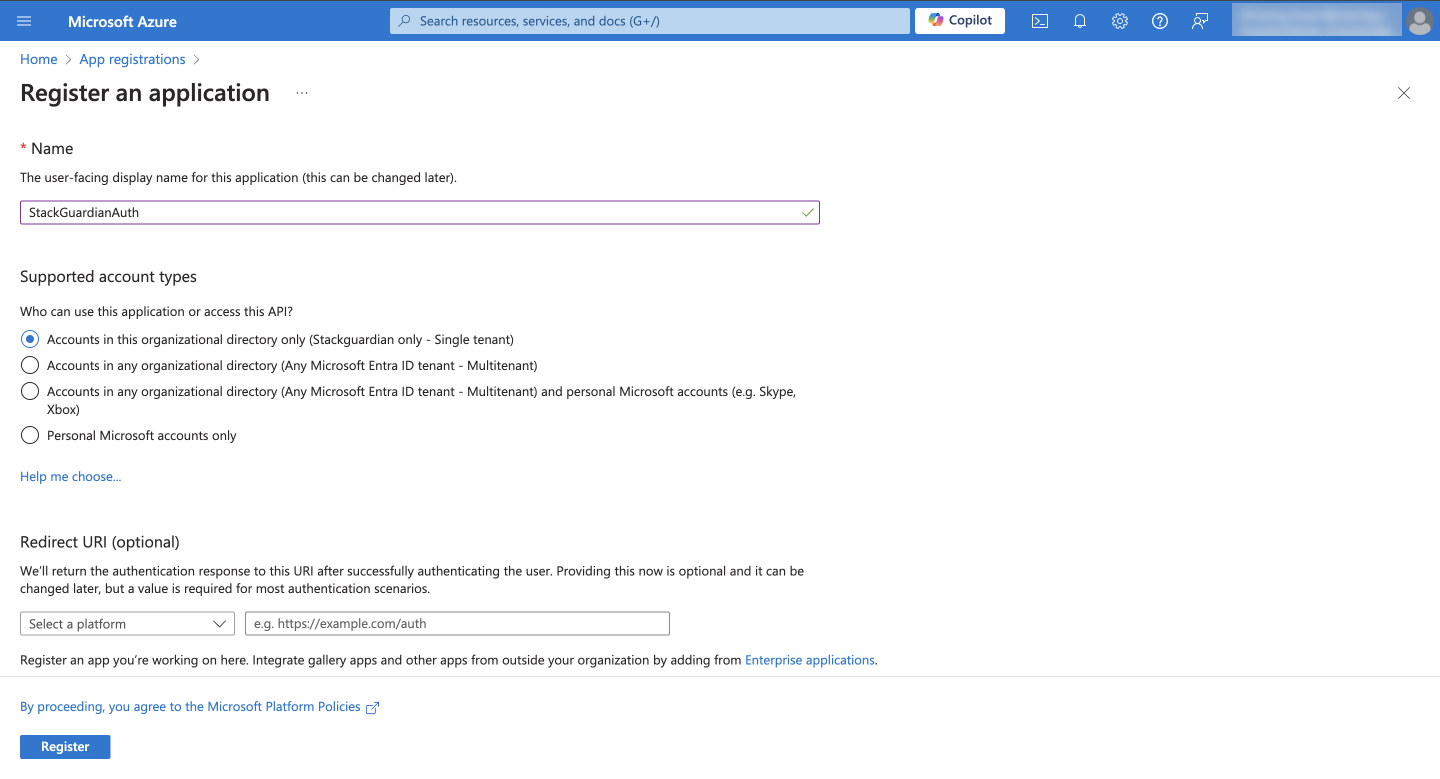
Step 1: Creating the App Registration
-
Under Microsoft Entra ID, navigate to App Registrations and click New registration.
-
Enter the following and click Register:
- Name: StackGuardianAuth
- Supported Account Types: Accounts in this organizational directory only
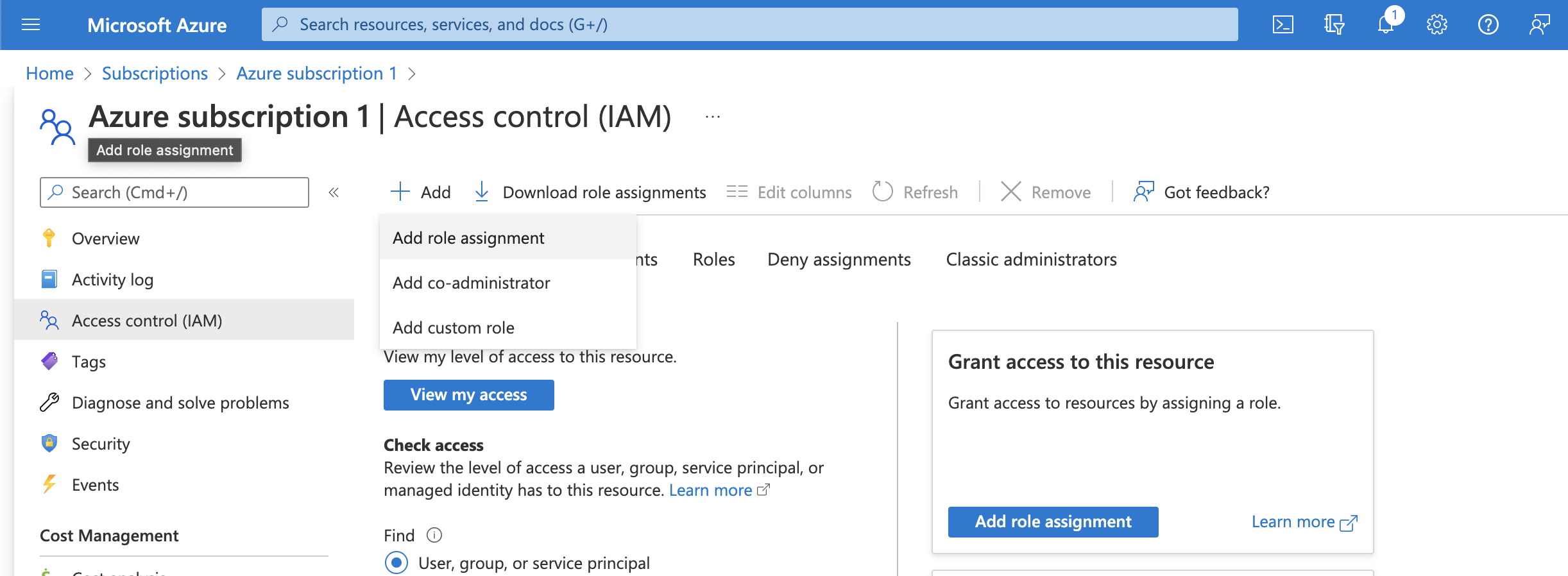
Step 2: Granting Appropriate Permissions to the Application
-
Navigate to Subscriptions through the search box or the left sidebar.
-
Click on the subscription you want to deploy into.
-
Select Access control (IAM) and click Add > Add role assignment:
-
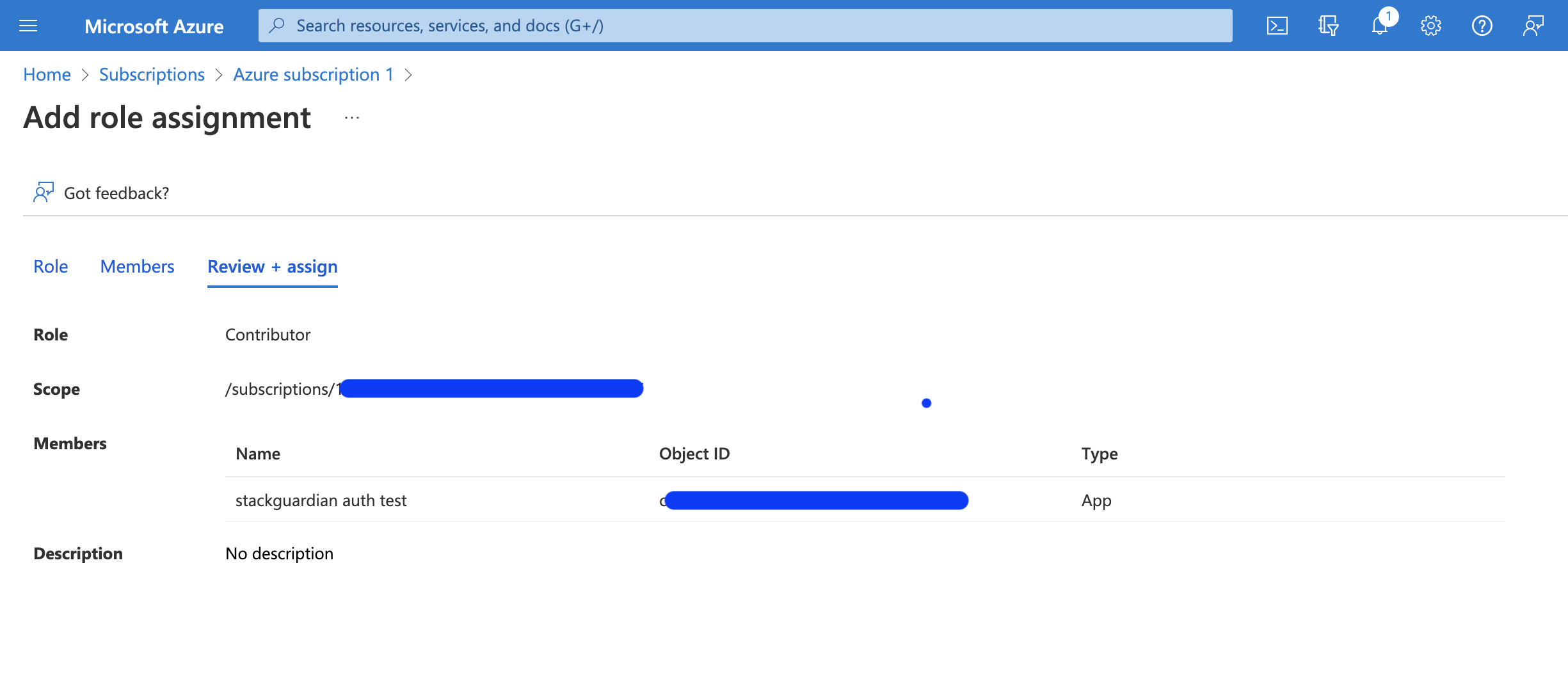
Choose a suitable role under "Role":
- "Contributor" provides read and write access.
- "Reader" offers read-only access.
Then, under "Select", choose the application created earlier and click "Review + assign".
-
Repeat this process for any additional subscriptions you want StackGuardian to manage.
Single Connector
The Single Connector approach is suitable for organizations managing a single Azure account. It simplifies the integration process with Azure.
- Navigate to Orchestrator > Connectors tab in StackGuardian.
- Click on Connect with Cloud Provider and proceed with the Azure configuration.
Completing the Azure Connector Setup
The following methods can be used to connect an Azure Service Principal, catering to different security and operational preferences:
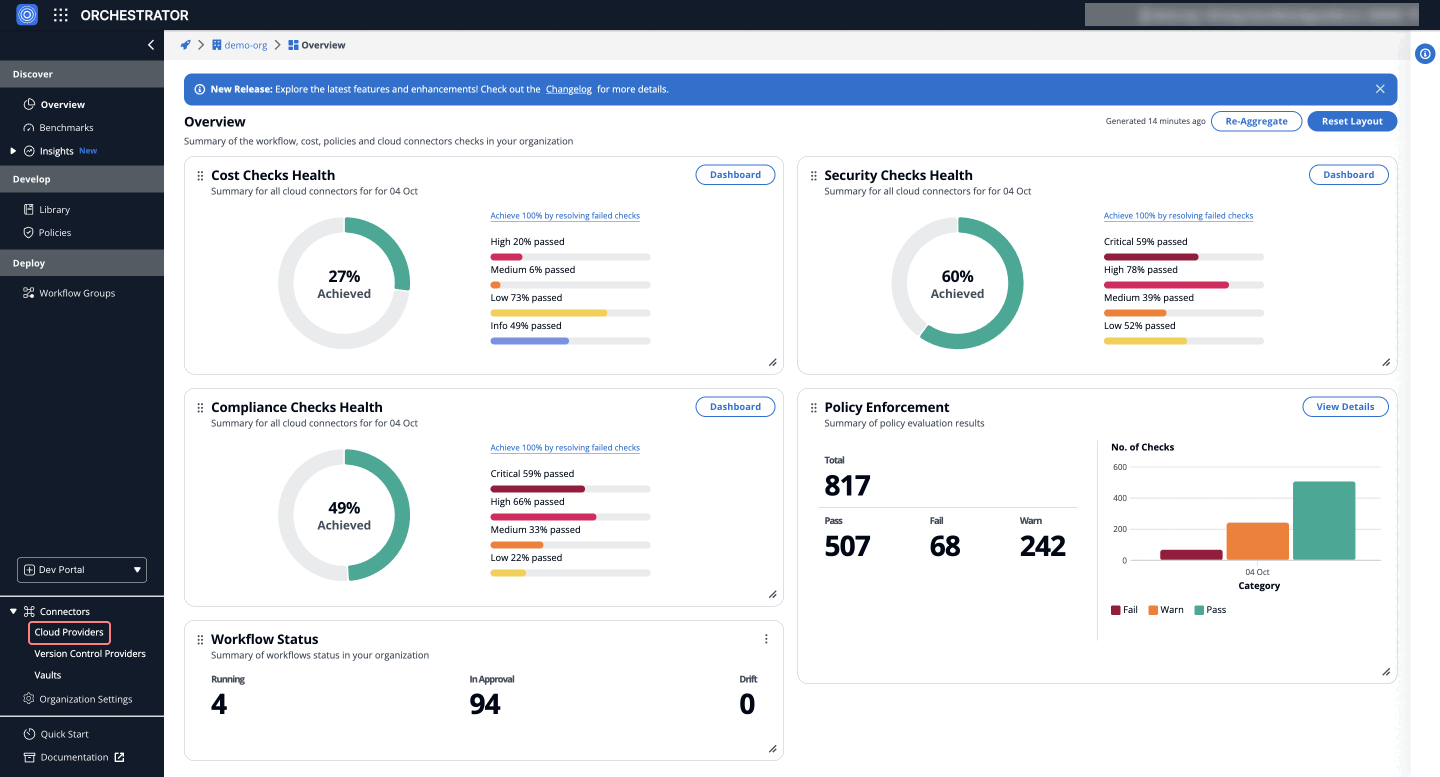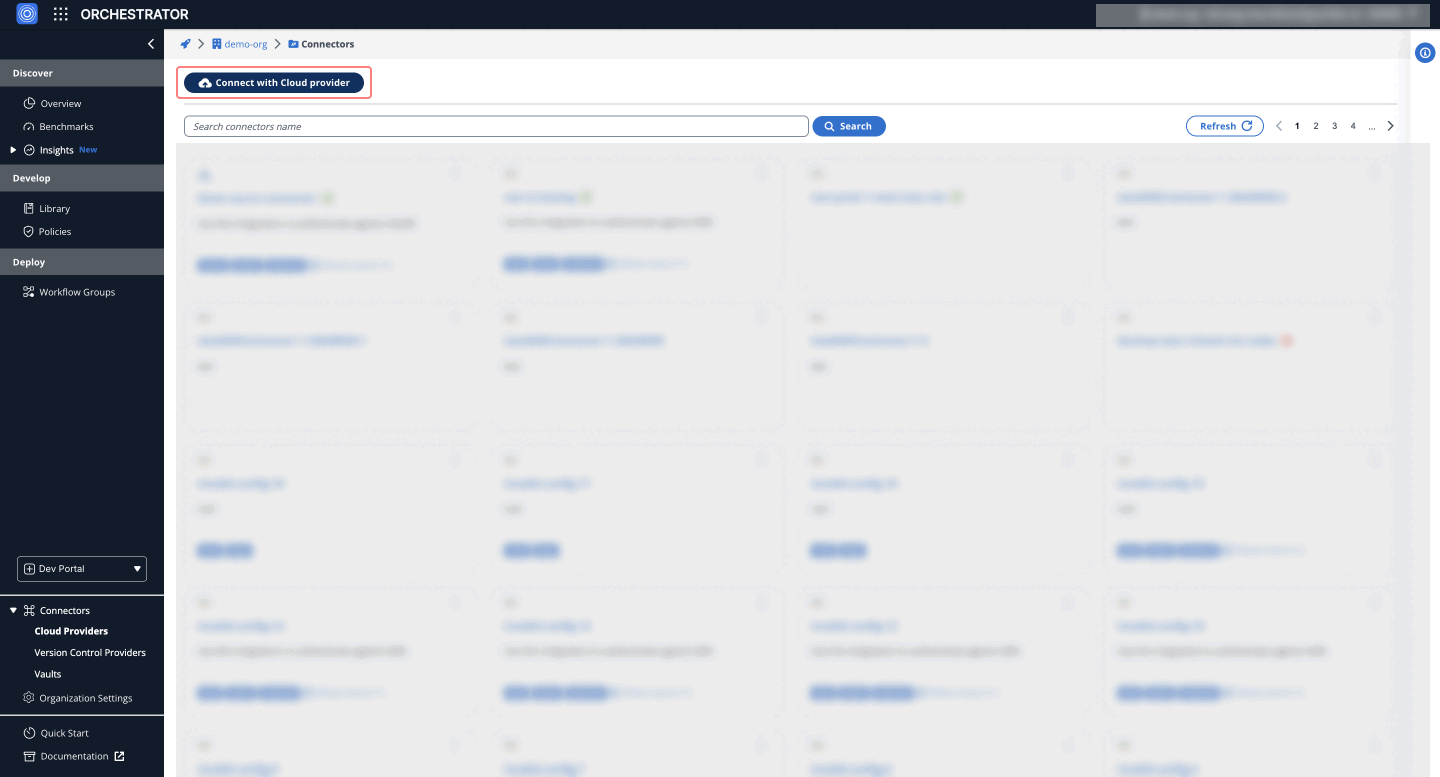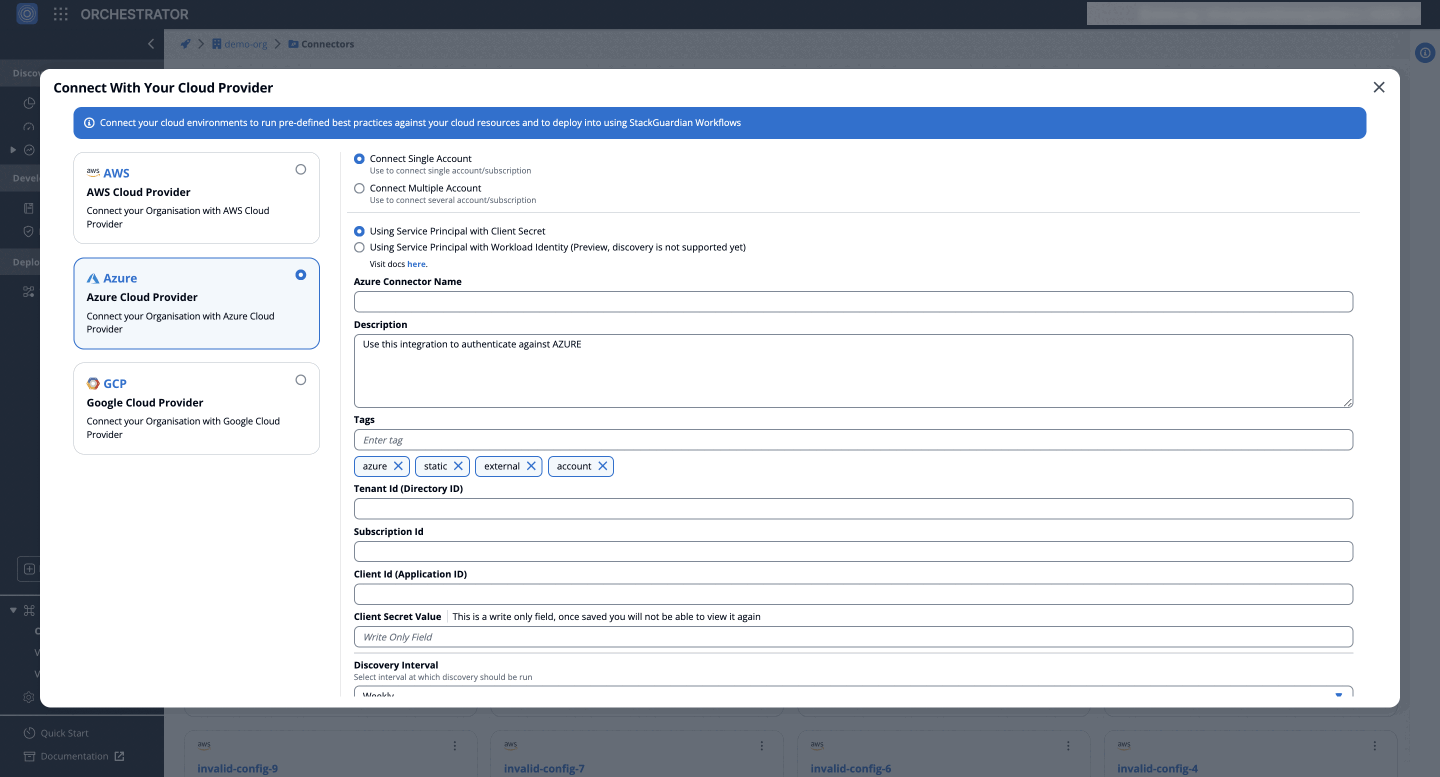
Service Principal with Client Secret
To finalize the connector configuration in StackGuardian using a Client Secret:
-
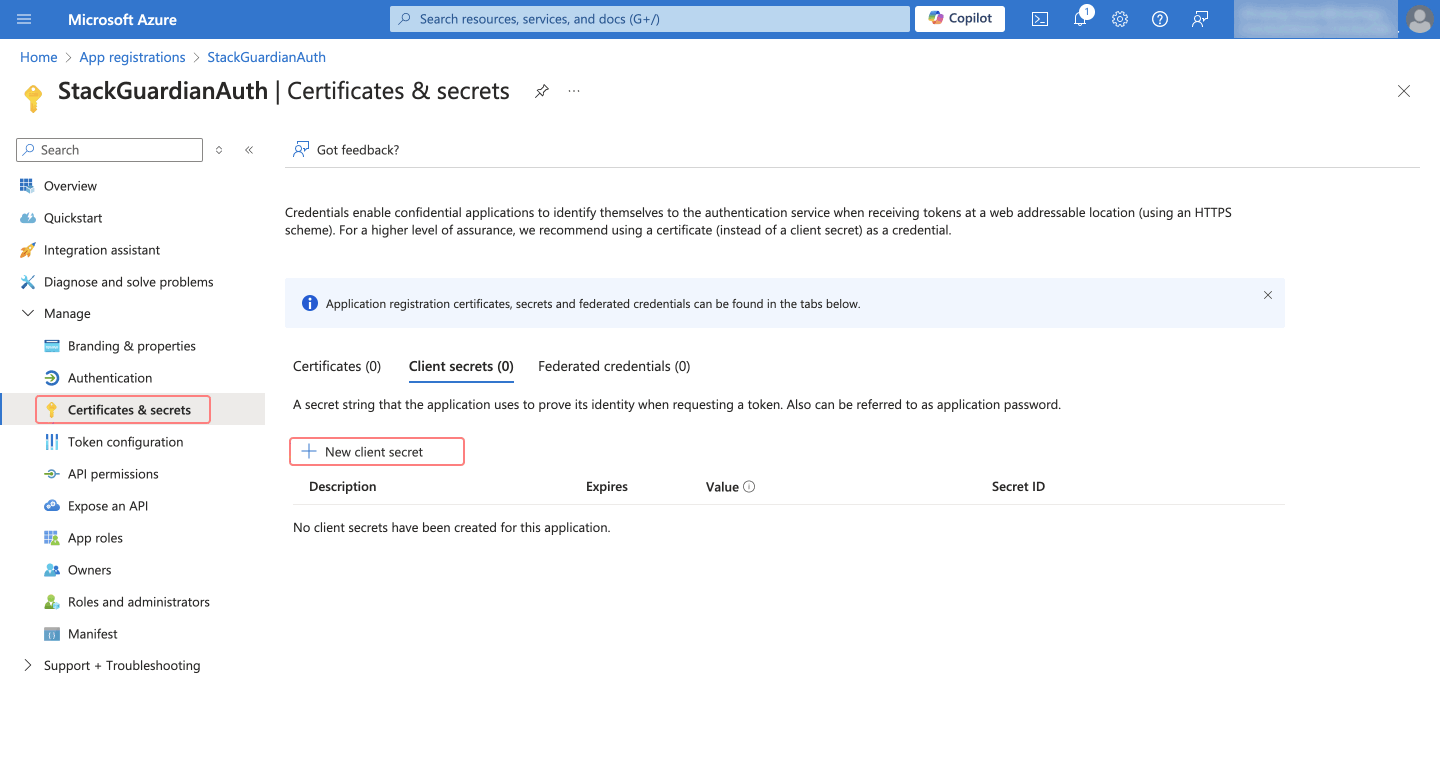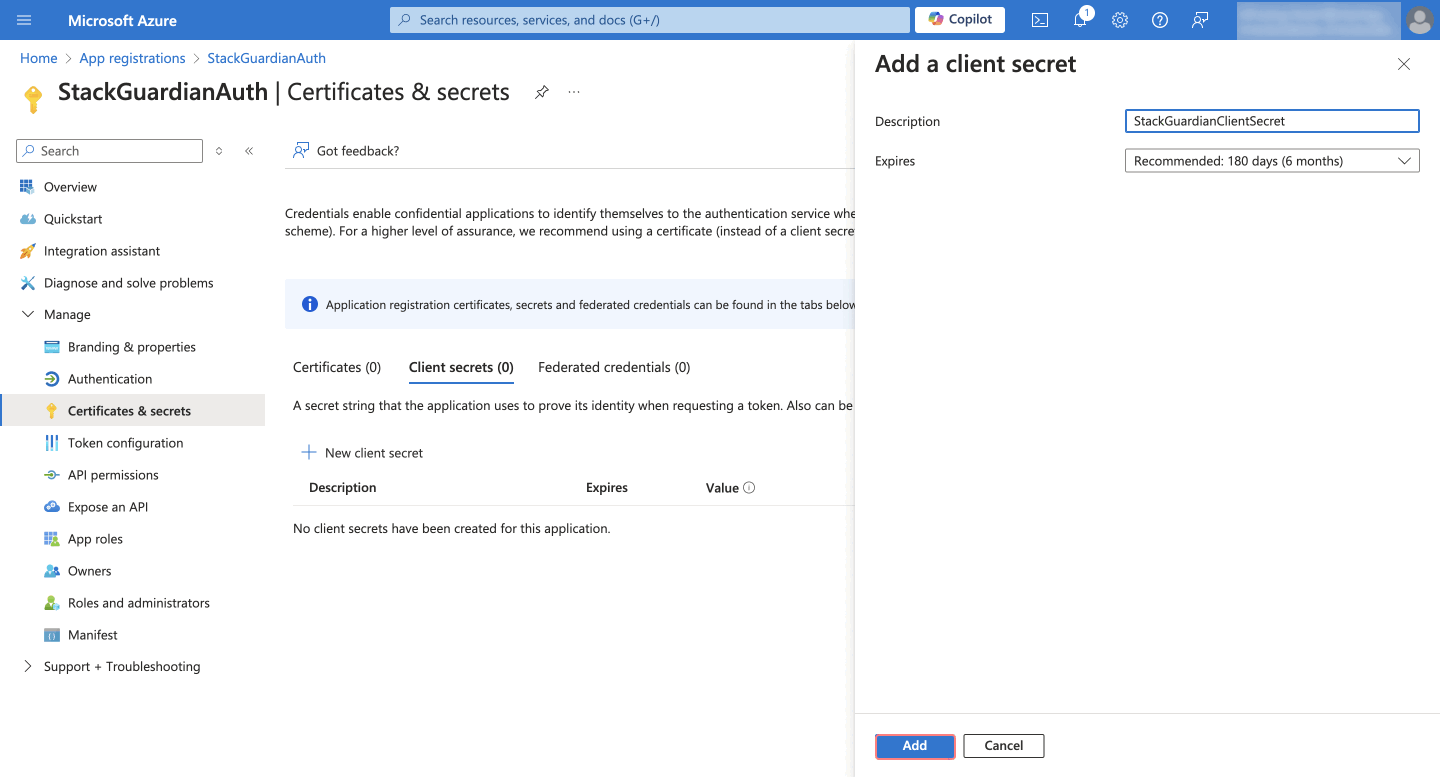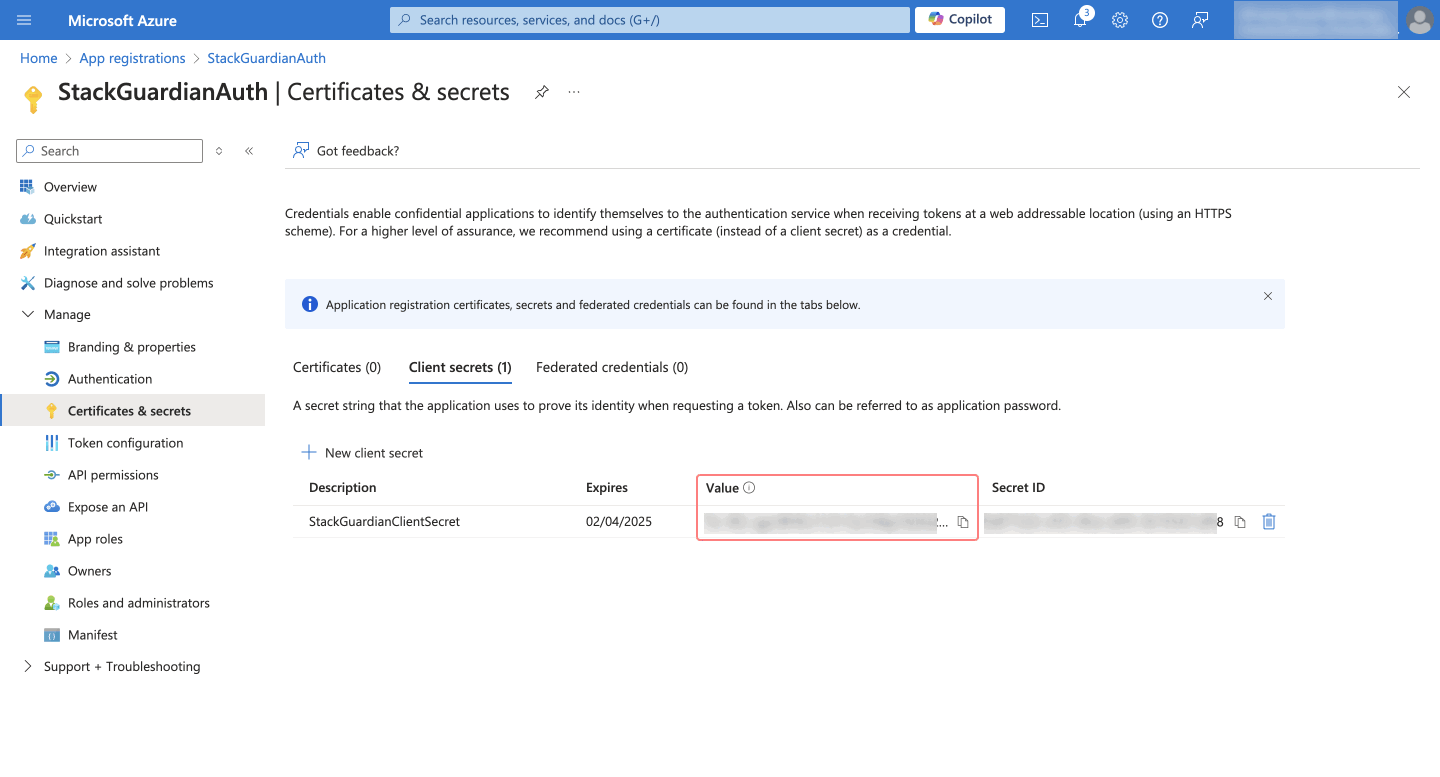
Create a Client Secret in Microsoft Entra ID:
- Navigate to Microsoft Entra ID in the Azure portal.
- In App Registrations, select the application you created (e.g.,
StackGuardianAuth). - Under Manage > Certificates & Secrets, click New client secret.
- Provide a Description, select an expiration period, and click Add.
- Copy the client secret value immediately.
-
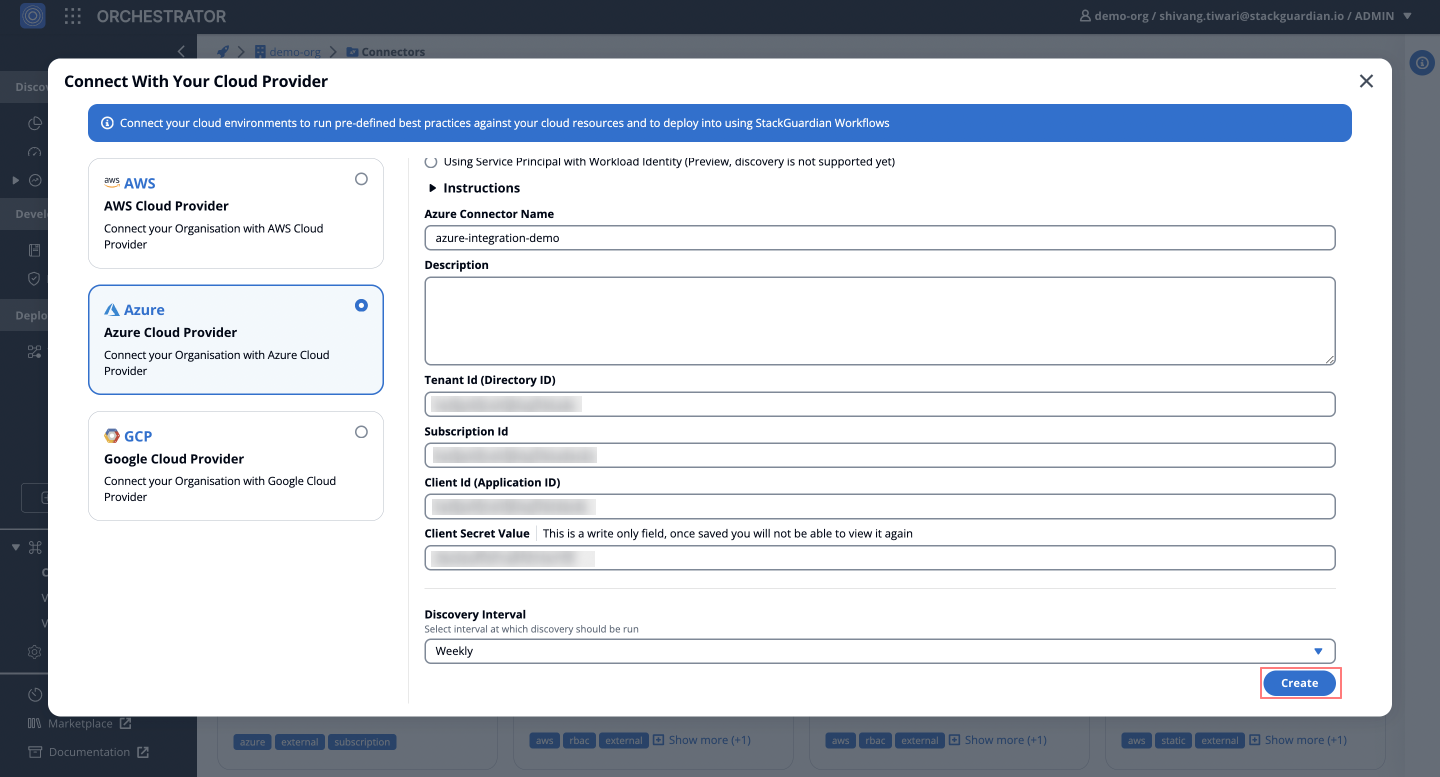
Use the Client Secret in StackGuardian’s Azure Connector:
- Navigate to the Orchestrator tab in StackGuardian and click Connectors.
- Select Azure and provide:
- Azure Connector Name
- Description
- Tenant ID (Directory ID)
- Subscription ID
- Client ID (Application ID)
- Client Secret Value
- Enable Periodic Discovery Checks if required.
- Click Create to finalize.
Service Principal with Workload Identity
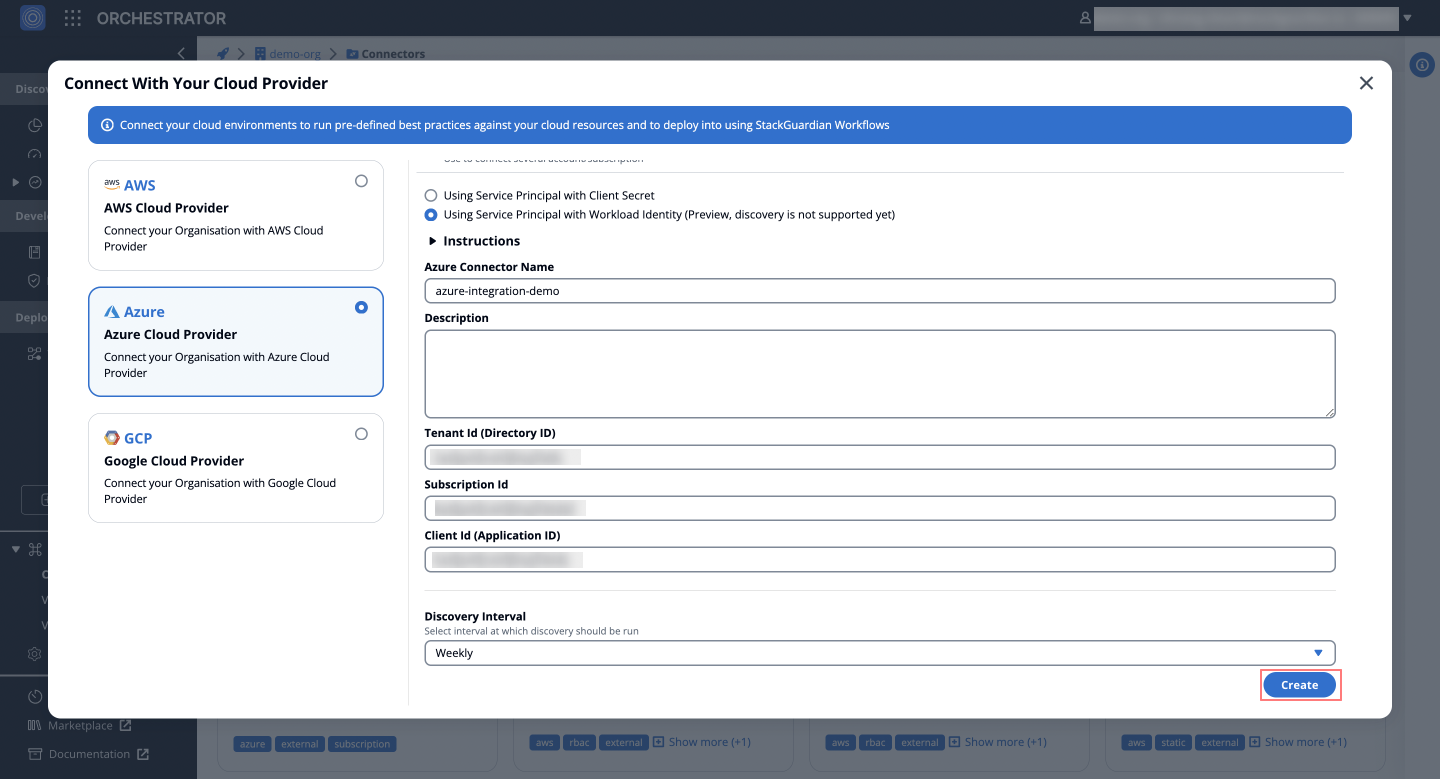
Using Workload Identity via OpenID Connect (OIDC) avoids managing client secrets. It allows StackGuardian to authenticate with Azure using a trusted identity provider.
-
Create a new App Registration in Azure named
sg-oidc-federation-test. -
Go to Certificates & secrets > Federated credentials, and click Add credential.
- Federated Credential Scenario: Select "Other issuer".
- Issuer:
https://api.app.stackguardian.io. - Subject Identifier:
/orgs/<YOUR_SG_ORG>. - Name: An appropriate identifier.
- Audience:
https://api.app.stackguardian.io.
-
Finalize the Azure Connector configuration in StackGuardian:
- Provide Tenant ID, Subscription ID, and Client ID.
- Optionally, enable "Periodic Discovery Checks".
- Click Create.
Group Connector
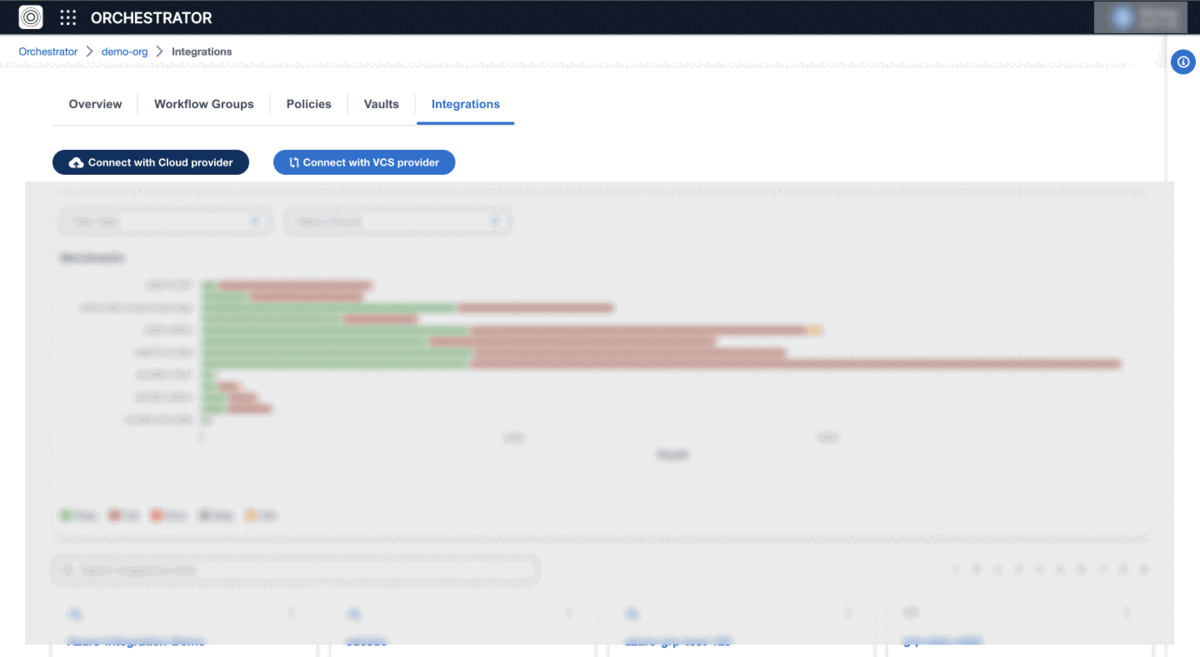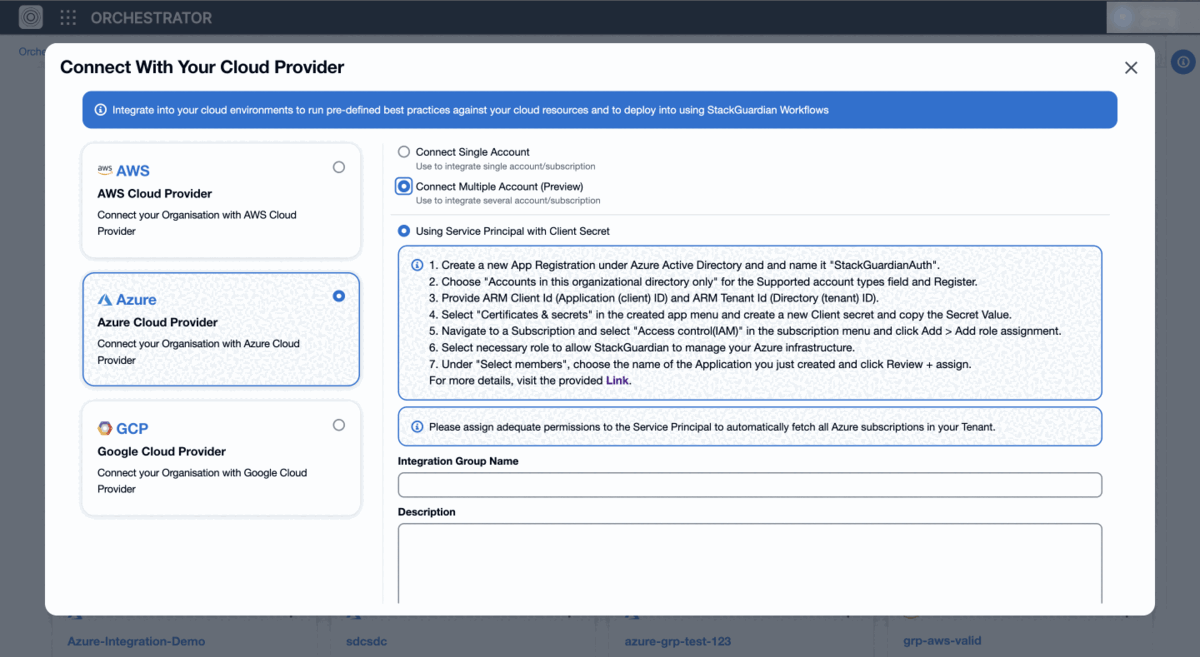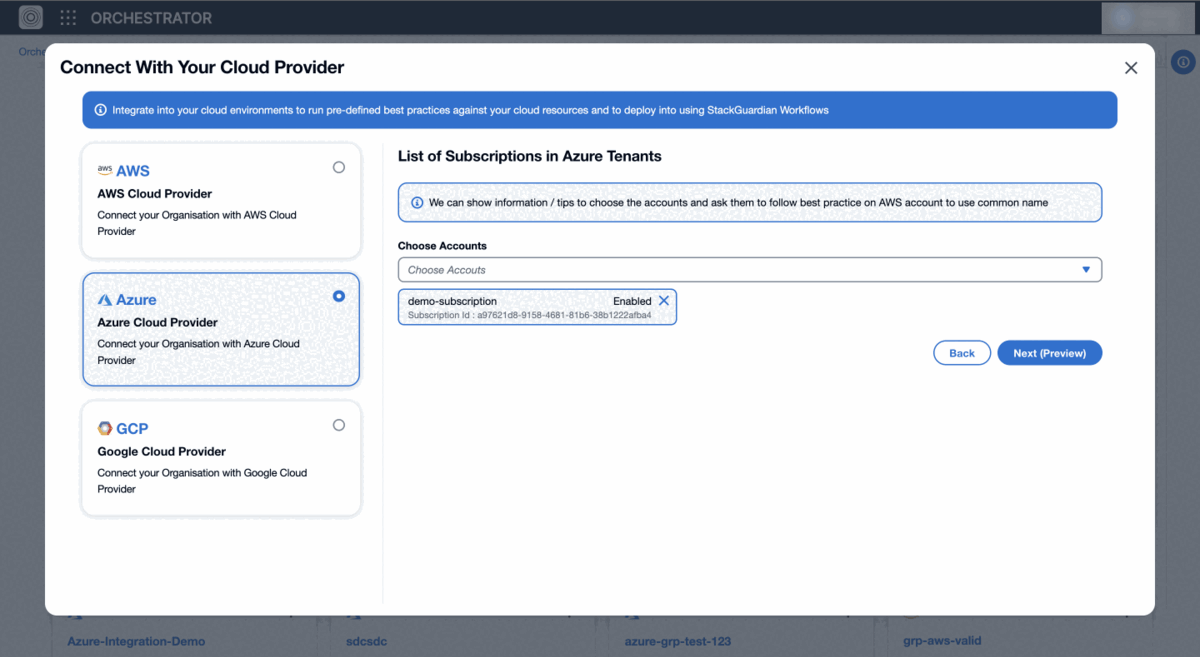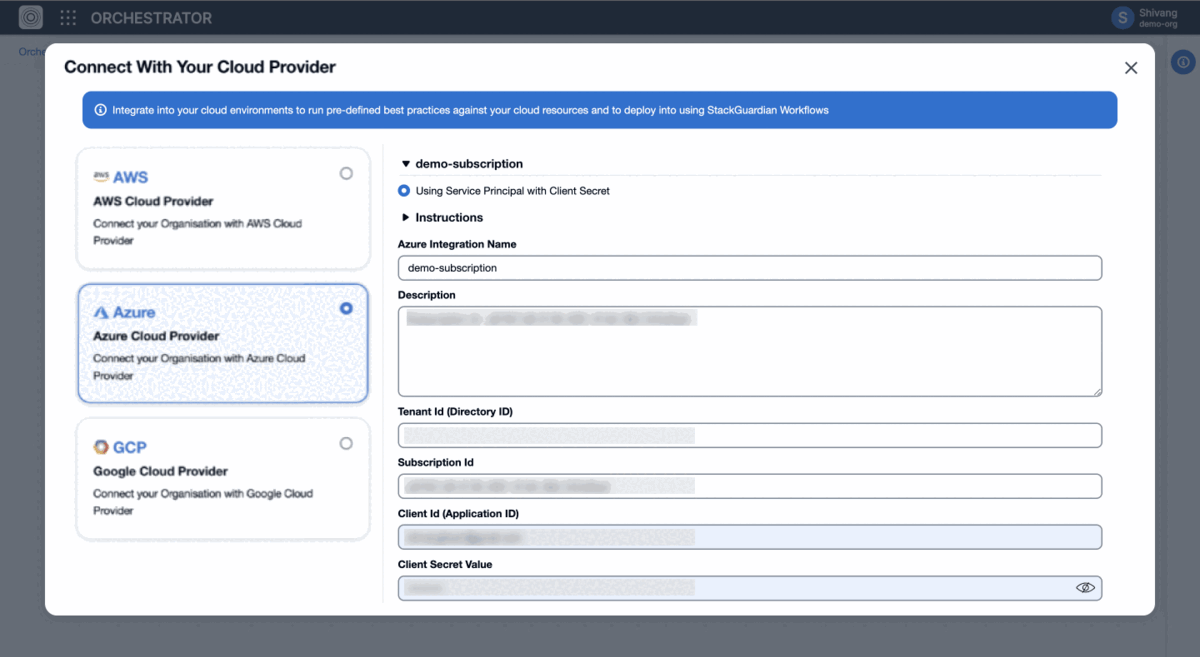
Group Connectors allow users to connect multiple Azure accounts, simplifying the onboarding process for organizations with multiple accounts.
How Group Connectors Work
- Log in to StackGuardian and navigate to the Connectors tab.
- Click on Connect with Cloud Provider.
- In the modal, select "Connect Multiple Account (Preview)".
- Enter a Connector Group Name and Description.
- In Azure Portal:
- Navigate to App Registrations and select the application.
- Copy the Application ID and Directory ID.
- Enter Tenant ID and Subscription ID.
- Click Next to view "List of Subscriptions in Azure Tenants".
- Choose accounts individually or select "Select All" to include Subscription IDs.
- Click Next (Preview) and configure the Global Settings:
- Tenant ID
- Client ID
- Client Secret Value
- For each subscription, provide:
- Azure Connector Name
- Description
- Tenant ID
- Subscription ID
- Client ID
- Client Secret Value
- Click Add All (Preview).
Enable "Periodic Discovery Checks" for monitoring if needed. Access and edit the Group Connector configuration as required.
Compliance and Security Best Practices
- Use Role-Based Access Control (RBAC): Ensure roles and permissions are minimal and precise.
- Monitor Resources: Enable continuous discovery checks for real-time monitoring of resources.
- Use Workload Identity: Prefer this method for higher security, avoiding secret management.
Additional Information
For further details, visit: