AWS
StackGuardian provides three main approaches for authenticating your workloads or running discovery against an AWS account:
Roles or RBAC (recommended)
In this guide, we'll walk you through the process of adding two StackGuardian AWS account IDs (476299211833 and 163602625436) to establish cross-account access using AWS IAM roles.
A pre-configured CloudFormation template can be used to create an IAM role with custom or AWS managed policies. This allows for the role and policy to be set up without accessing the StackGuardian platform. Create IAM Role with CloudFormation
Creating a New IAM Role
-
Create a New Role in the AWS IAM Console:
- Navigate to the AWS IAM Console.
- Select "Roles" in the left-hand menu.
- Click on the "Create Role" button.
-
Configure the Role:
- Choose the trusted entity type as "Another AWS account."
- For Account ID, enter 476299211833 (StackGuardian’s Account ID).
- Set the role's permissions by attaching the ReadOnlyAccess policy, allowing StackGuardian to list, describe, and assess resources. For deployment needs, include additional permissions for reading, writing, updating, and deleting, tailored to specific requirements.
- Ensure "Require external ID" is selected.
- Set the External ID to match the format
<org-name>:<random-string>or<org-name>-<random-string>. For example, 'myorg:abc12345'. - Leave "Require MFA" disabled.
-
Add Tags and Role Information:
- Optionally, provide tags for the role to categorize and manage it.
- Give the role a descriptive name like 'StackGuardianIntegrationRole'.
- Add an appropriate description for the role.
-
Create the Role:
- Review the configuration and click the "Create Role" button.
Adding the Second StackGuardian AWS Account
For cross-account access via AWS IAM roles, adding a second account is necessary. After creating the role, follow these steps to incorporate the second account:
-
Edit Trust Policy:
- Go to the Role you created and click on "Trust Relationship."
- Click on "Edit trust policy."
-
Modify JSON Statement:
- In the JSON statement, under "Principal > AWS," add the Account ID of the second StackGuardian AWS account (163602625436).
Example Trust Policy:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"AWS": [
"arn:aws:iam::476299211833:root",
"arn:aws:iam::163602625436:root"
]
},
"Action": "sts:AssumeRole",
"Condition": {
"StringEquals": {
"sts:ExternalId": "myorg:abc12345"
}
}
}
]
}Update the Policy
After adding the second account ID, click on "Update Policy."
Access Keys
- Create a new user in the AWS IAM Console.
- Provide a user name and select "Access key - Programmatic access" for the AWS access type.
- Attach necessary policies to allow StackGuardian to manage your AWS infrastructure.
Using OIDC Identity Provider
Integrating OpenID Connect (OIDC) with StackGuardian streamlines secure access to AWS resources by allowing users to authenticate using existing credentials from an external Identity Provider (IdP). This setup bolsters security by minimizing direct credential management and enhances efficiency by enabling StackGuardian users to assume AWS IAM roles for necessary operations.
1. Identity Provider Setup
In the AWS IAM Console, begin by creating the identity provider:
- Choose "Add Provider".
- Select "OpenID Connect" and enter the Provider URL and Audience as
https://api.app.stackguardian.io. - Finally, add the provider by clicking "Add provider".
2. IAM Role Creation
Create an IAM Role:
- Choose the trusted entity as "Web Identity".
- Under "Choose a provider", select
api.app.stackguardian.io. - Set the Audience to the StackGuardian API base URL:
https://api.app.stackguardian.io. - Click "Next" and assign the required permissions to the role.
- For using the discovery functionality in StackGuardian, the ReadOnlyAccess permissions are sufficient.
- For deployment via StackGuardian, choose the least permissions required for your needs.
- Name the role and click "Create Role".
3. Trust Policy Configuration
Update the Trust Policy for federated login:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Federated": "arn:aws:iam::<YOUR_AWS_ACCOUNT_ID>:oidc-provider/api.app.stackguardian.io"
},
"Action": "sts:AssumeRoleWithWebIdentity",
"Condition": {
"StringEquals": {
"api.app.stackguardian.io:aud": "https://api.app.stackguardian.io"
},
"StringLike": {
"api.app.stackguardian.io:sub": "/orgs/<YOUR_SG_ORG>"
}
}
}
]
}
<YOUR_AWS_ACCOUNT_ID> should already show your AWS account ID but update the policy with your StackGuardian organization name <YOUR_SG_ORG>.
4. Finalize Configuration
Confirm the setup and copy the Role ARN for the final step.
Single Connector
The Single Connector approach is suited for organizations managing a single AWS account. This method streamlines the integration process with AWS.
- Begin by navigating to Connectors > Cloud Providers in StackGuardian.
- Click "Connect with Cloud Provider" to start the configuration process.
- Follow the subsequent steps to set up your AWS connector.
Completing the Connector
Using RBAC
After creating an IAM role and establishing cross-account access:
- Retrieve Role ARN and External ID: Note the Amazon Resource Name (ARN) and External ID of the newly created role. These are crucial for additional security when assuming the role.
- Navigate to the AWS connector form in StackGuardian and input the Role ARN and External ID.
Using Access Keys
Once in the AWS console, after creating the user with added policies and necessary permissions, provide the generated Access key ID, Secret access key, and Default AWS region below.
OIDC Identity Provider
After creating an IAM role:
- Navigate to Connectors > Cloud Providers in StackGuardian and click "Connect with Cloud Provider" to start the configuration process.
- Add a Connector name and input the role ARN copied in the previous step. Click "Create" to finalize the connector.
Group Connector
Group Connectors allow users to connect multiple AWS accounts instead of connecting them individually, simplifying the onboarding process for organizations with a large number of accounts.
How Group Connectors Work
Here are the steps to create a Group Connector:
-
Log in to the StackGuardian Platform and navigate to the Connectors > Cloud Providers tab and click on "Connect with Cloud provider".
-
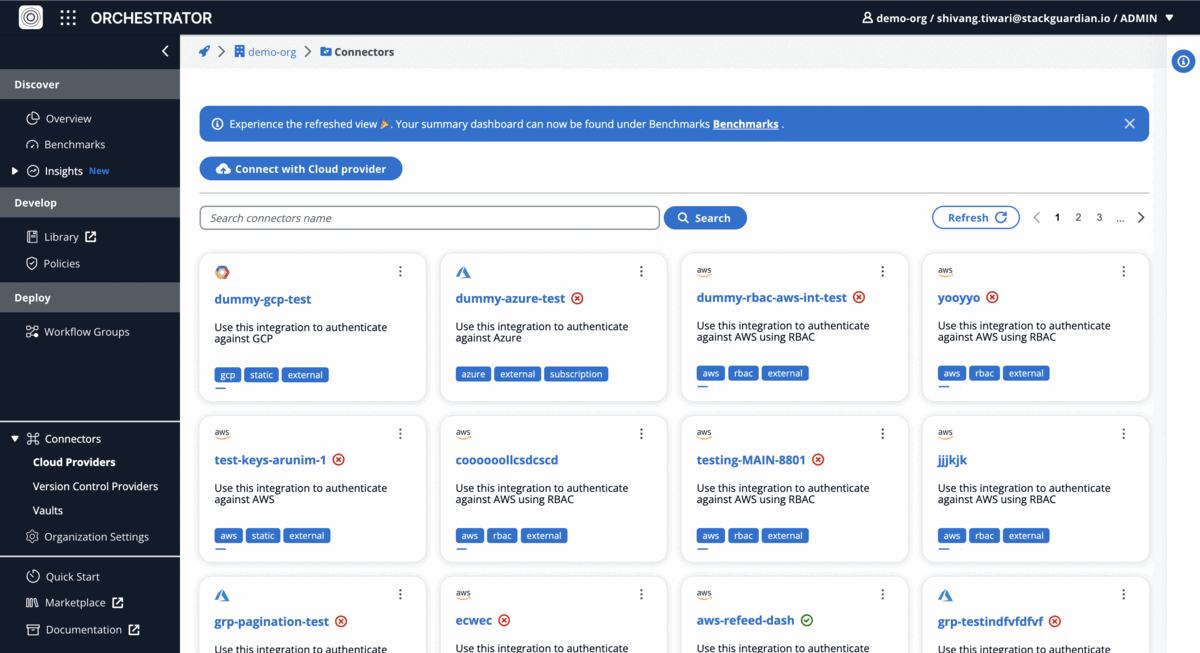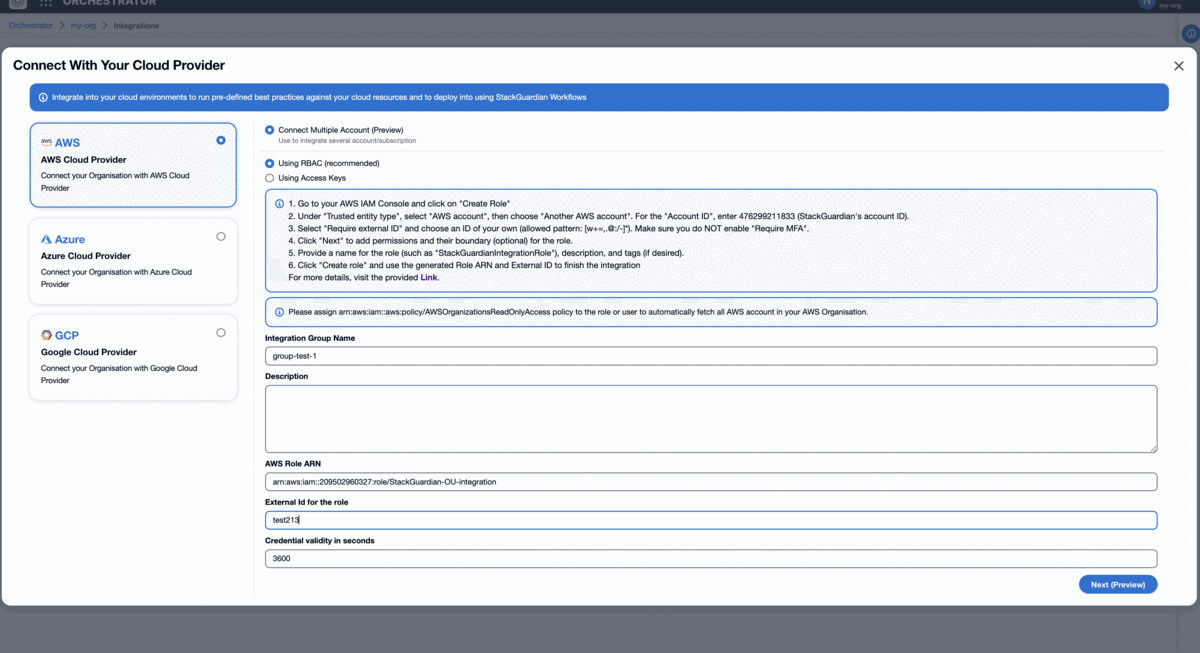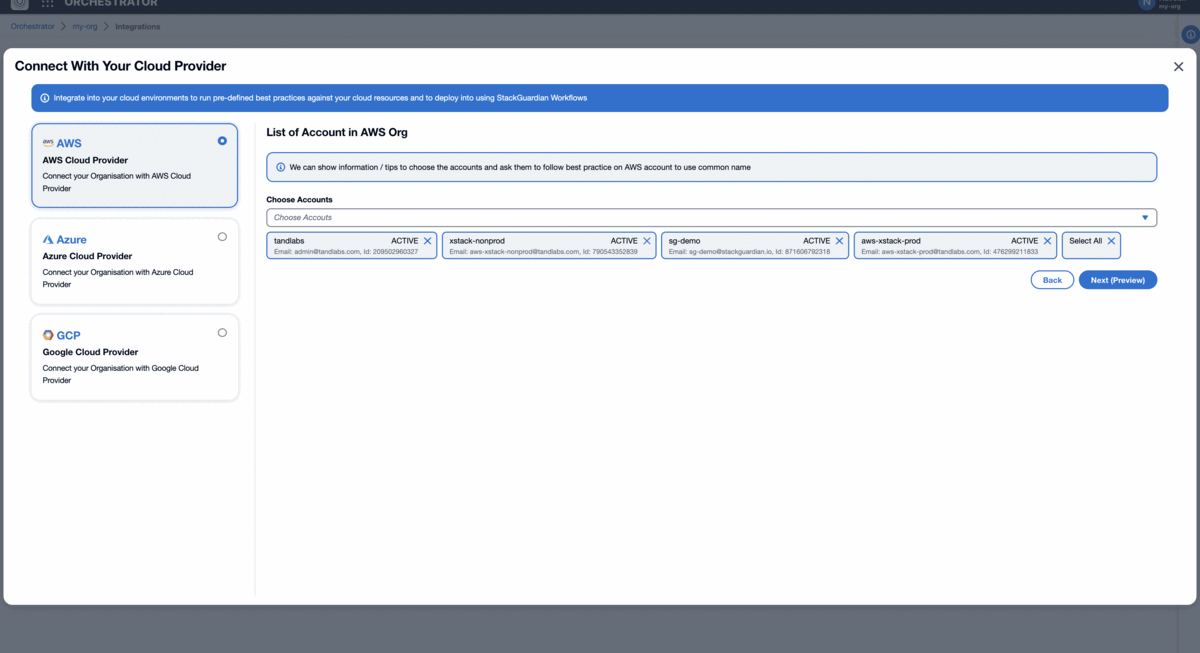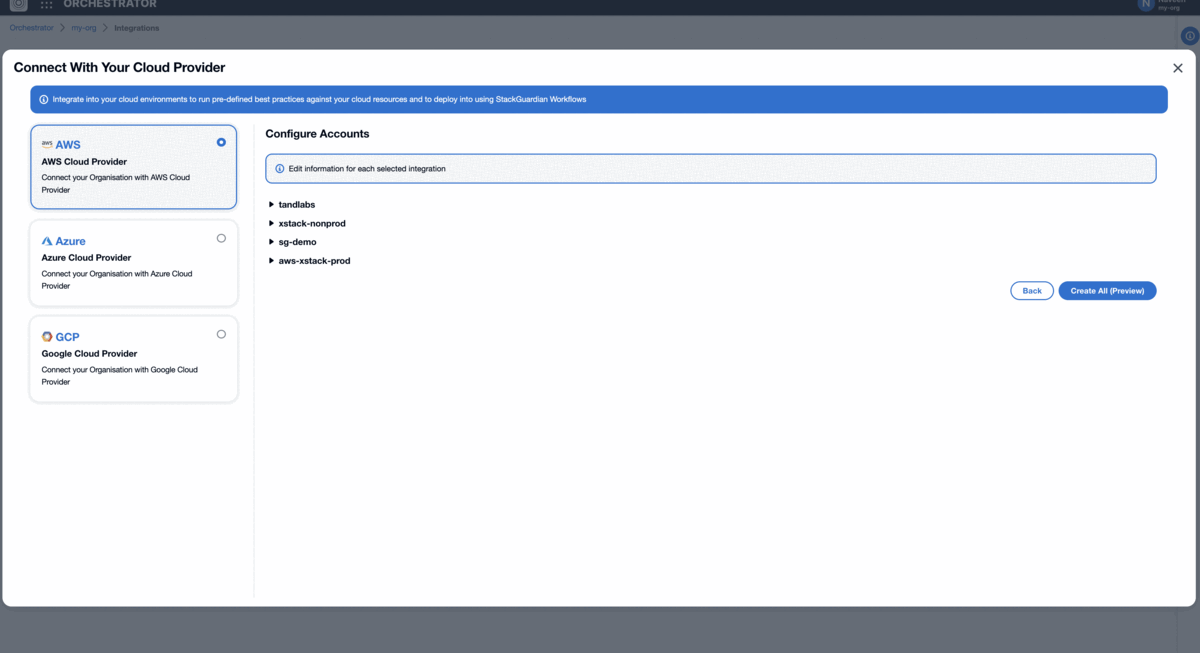
In the connectors modal, select "Connect Multiple Account (Preview)".
-
Choose one of the two ways to configure AWS connectors: "Roles or RBAC" (recommended) or "Access Keys".
-
Enter a Connector Group Name and a Description for the Group connector (e.g., "Enterprise AWS Accounts").
-
Provide the AWS Role ARN and External ID for the role associated with the connector. Ensure the format for the external ID is
<org-name>:<random-string>or<org-name>-<random-string>. Ensure you match this format (allowed pattern:[\\w+=,.@:/-]*). Make sure you leave Require MFA disabled. For example, 'myorg:abc12345'. -
Click on the "Next (Preview)" button.
-
In the List of Accounts in AWS Org section, use the dropdown menu "Choose accounts" to select individual active users or "Select All" users in the organization. This will include the Email and Account ID details of the AWS accounts.
-
Click on "Next (Preview)". Under the Global Settings, set the IAM Role Name & AWS Default Region, which are common attributes for all connected accounts.
-
In the Configure Accounts section, you need to fill in the following fields for each account:
- AWS Connector Name: Provide a brief explanation of the connector's purpose.
- Description: Enter a concise description.
- AWS Role ARN: Specify the AWS role ARN.
- External Id for the role: Provide the external ID associated with the role.
- Credential validity in seconds: Specify the desired duration of credential validity.
-
To complete the connector setup, click on "Add All (Preview)".
You can now click on the newly created card with the Connector group name to access and edit the Group Connector account's configuration.
Group Connectors
Compliance Discovery
You can detect existing noncompliance and get recommendations by running StackGuardian AWS Compliance Discovery against your AWS account by leveraging the configured connector.
- Click on the connector you want to detect noncompliance in.
- Select the region and click on the
Run Discoverybutton.
- The compliance discovery results will become available in about 10 mins in the same view.
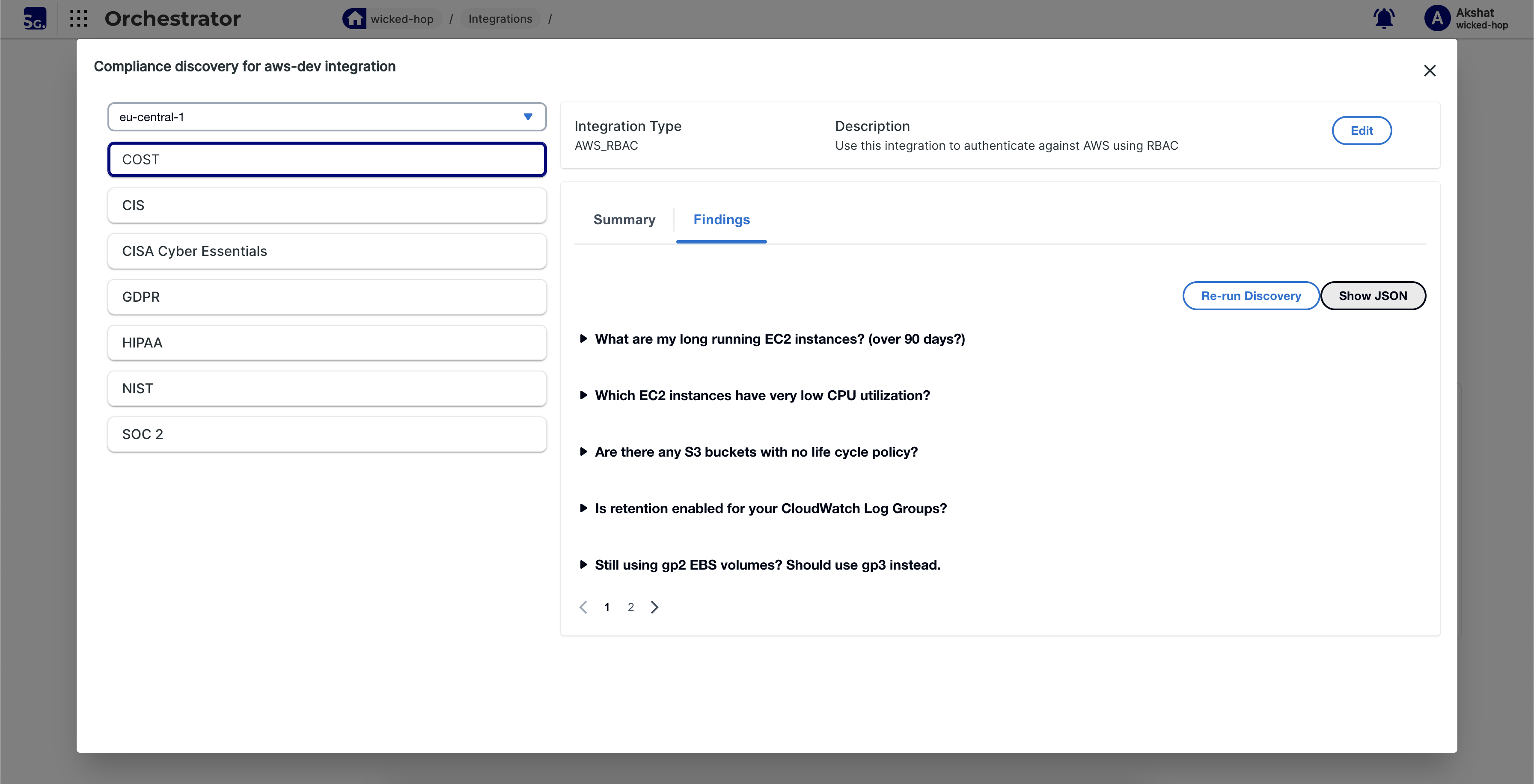
Supported Checks
Visit the StackGuardian Marketplace for a comprehensive list of supported reactive checks and request new features.